© NinoSec
| All Rights Reserved
NinoSec
| All Rights Reserved
Azure SIEM + Honeypot
The goal of the project was to set up a Windows Virtual Machine and intentionally make it vulnerable by disabling the firewall and port security in Network Security Group (NSG).
By exposing the machine to the internet, I was able to monitor and track the IP addresses of potential attackers.
Using a custom PowerShell script, I extracted metadata from the Windows Event Viewer logs. This data was then forwarded to a third-party API to derive geolocation information based on the attackers' IP addresses.
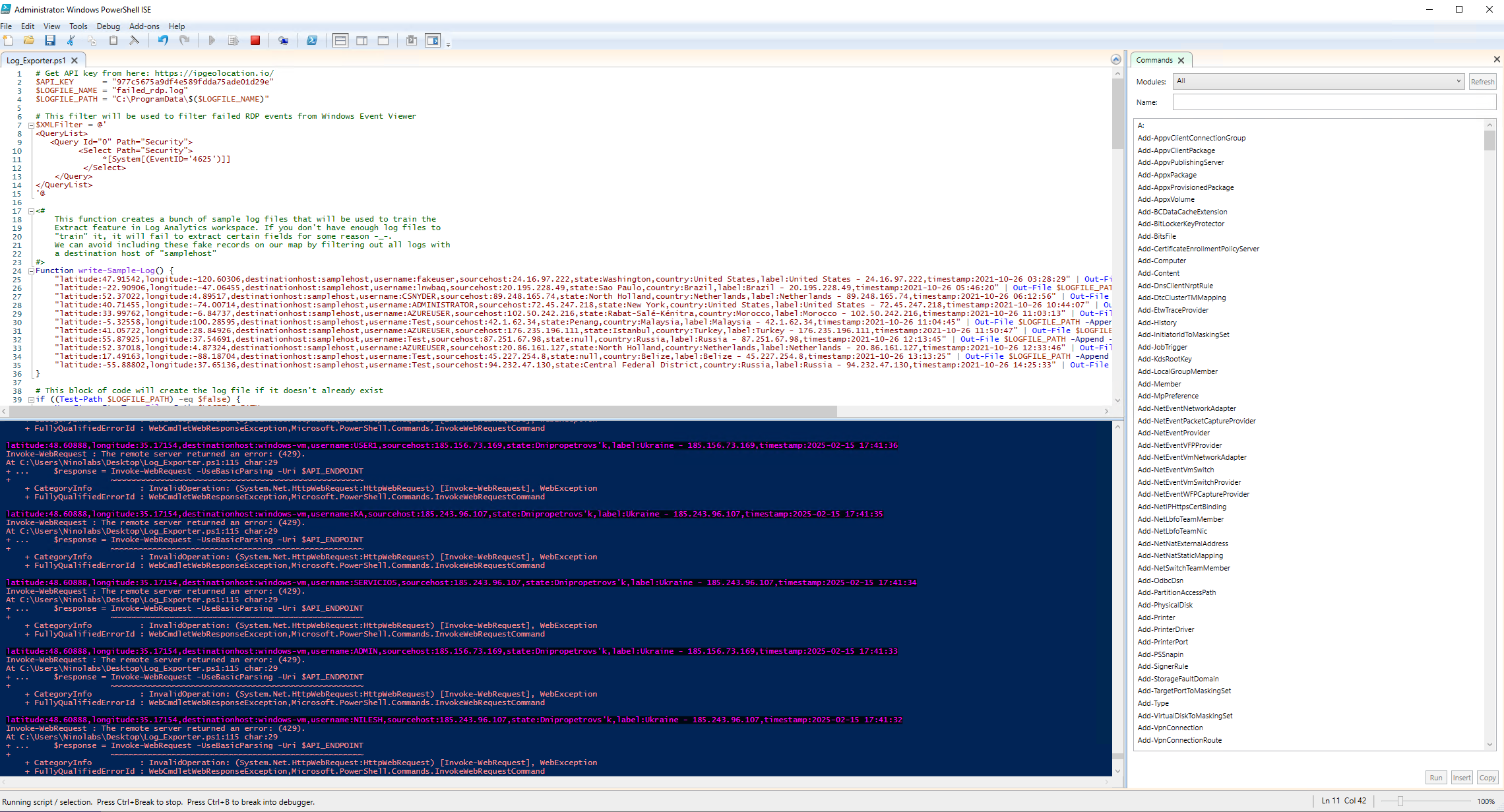
The attacks started coming in almost immediately, so I set up a Log Analytics Workspace in Azure to collect custom logs with location details like latitude, longitude, state/province, and country.
I created custom fields in the workspace to organize this location data. I also linked the failed_rdp.log file to the Log Analytics Workspace so the data could be analyzed in Azure Sentinel.
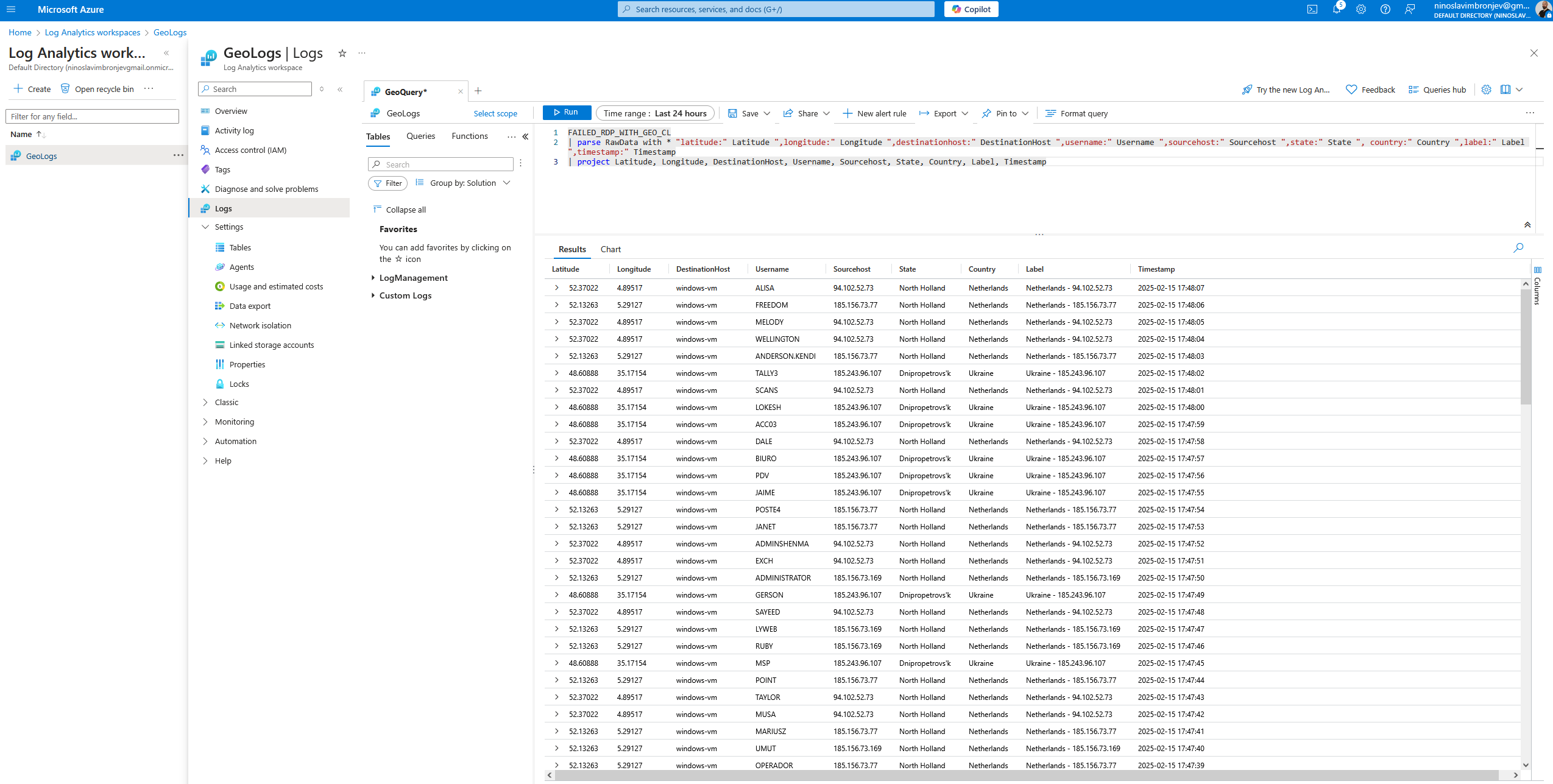
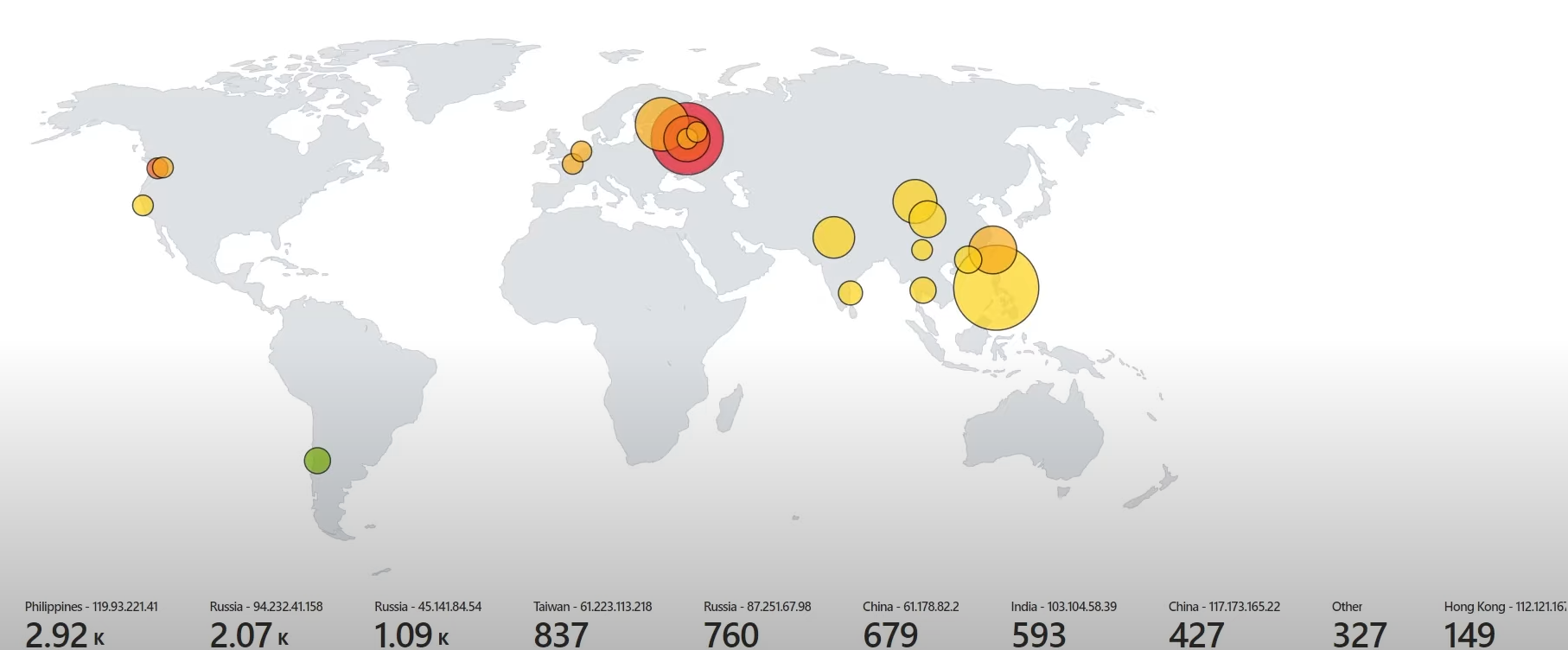
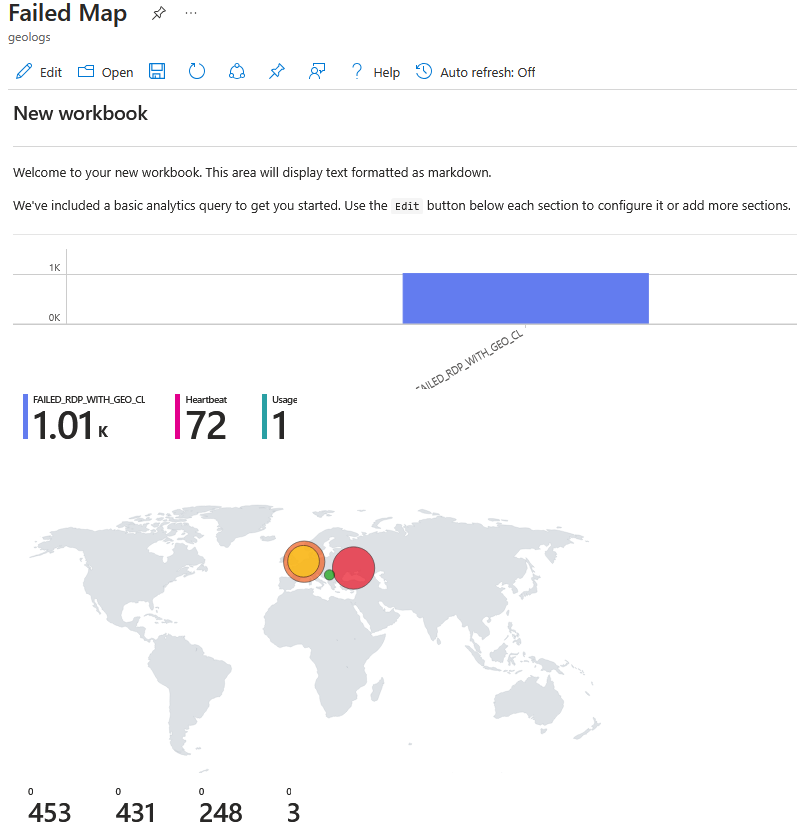
Configured Azure Sentinel (Microsoft's cloud-based SIEM) to create a workbook that visualizes global attack data, specifically RDP brute-force attempts.
The workbook displays the data on a world map, highlighting the physical locations and magnitude of the attacks.
After implementing the following code:
FAILED_RDP_WITH_GEO_CL
| extend username = extract(@"username:([^,]+)", 1, RawData),
timestamp = extract(@"timestamp:([^,]+)", 1, RawData),
latitude = extract(@"latitude:([^,]+)", 1, RawData),
longitude = extract(@"longitude:([^,]+)", 1, RawData),
sourcehost = extract(@"sourcehost:([^,]+)", 1, RawData),
state = extract(@"state:([^,]+)", 1, RawData),
label = extract(@"label:([^,]+)", 1, RawData),
destination = extract(@"destinationhost:([^,]+)", 1, RawData),
country = extract(@"country:([^,]+)", 1, RawData)
| where destination != "samplehost"
| where sourcehost != ""
| summarize event_count=count() by latitude, longitude, sourcehost, label, destination, country
We get the end result:
