© NinoSec
| All Rights Reserved
NinoSec
| All Rights Reserved
PowerShell File Integrity Monitor
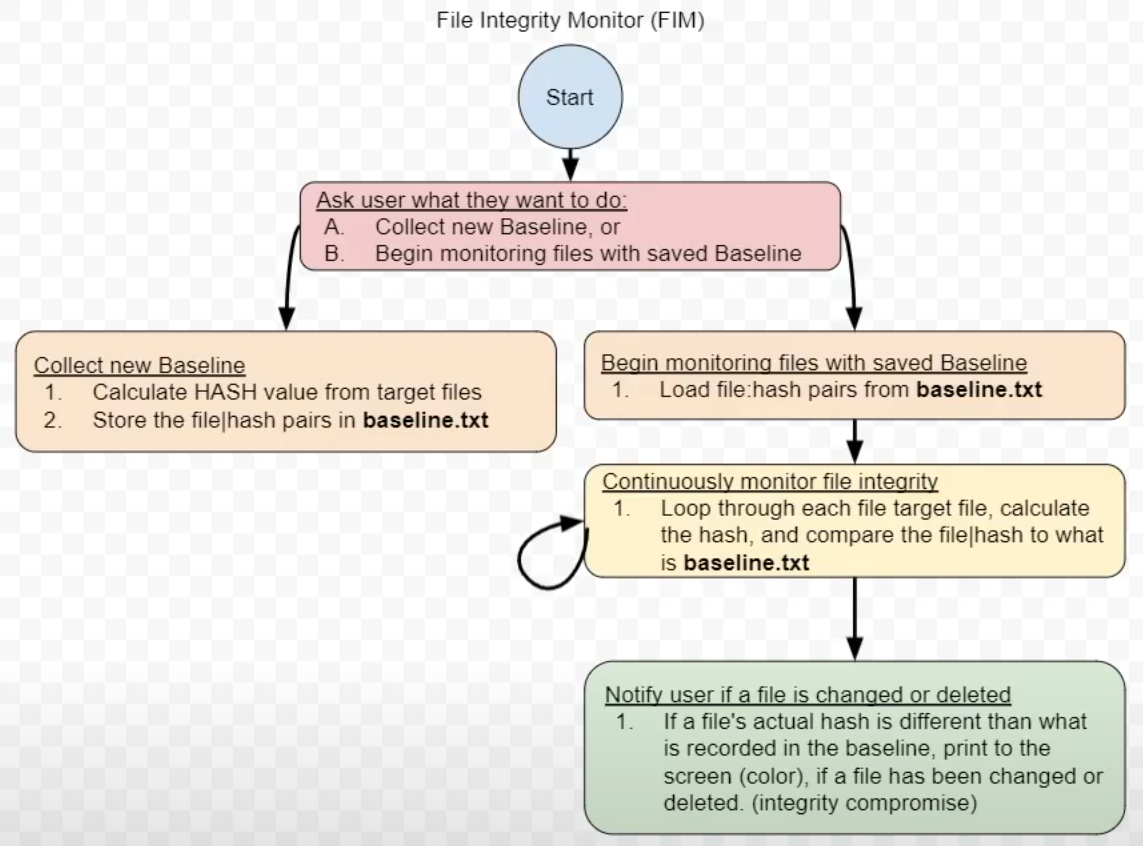
In today’s cybersecurity landscape, ensuring the integrity of critical files and directories is more important than ever.
Unauthorized changes to system files, configuration files, or sensitive data can lead to security breaches, compliance violations, and operational disruptions. To address this challenge, I decided to create a custom File Integrity Monitor (FIM) as a proof of concept.
This post walks you through the process, the challenges, and the lessons learned.
How It Works
Step 1: Creating the Integrity Baseline
The first step was to create a baseline of the target files and folders. I used the SHA-512 hashing algorithm to generate unique checksums for each file. This checksum acts as a fingerprint for the file’s content. Any change to the file (even a single byte) will result in a different checksum.
Step 2: Continuous Monitoring
Once the baseline was established, I implemented a monitoring loop to continuously compare the actual state of the files against the baseline. This involved:
Recalculating the SHA-512 checksum for each file.
Comparing the new checksum with the baseline checksum.
Detecting changes such as new files, modified files, or deleted files.
Step 3: Alerting
For this proof of concept, I kept the alerting mechanism simple by printing alerts to the console. In a production environment, this could be enhanced to send alerts via email, SMS, or integrate with a SIEM (Security Information and Event Management) system.
